Chromium SQLite Parser (csp)
Introduction
Google's Chrome Browser has many artifacts available that the forensics examiner can use in identifying a user's Internet activity. This includes Chrome's various databases, local storage, JSON formatted text files, and cache.
This tool, however, does not target all of Chrome's artifacts; it only targets certain SQLite databases and specific tables within those databases that are used by the Browser that have been deemed useful by the forensics community. Specifically, this tool targets the following seven databases: (a) History, (b) Cookies, (c) Web Data, (d) Top Sites, (e) Shortcuts, (f) Login Data and (g) Favicons.
The semantics to run this tool just requires one to use the -db option and pass in the path/file of the Chrome SQLite database to parse. The screenshot shows all the options available.
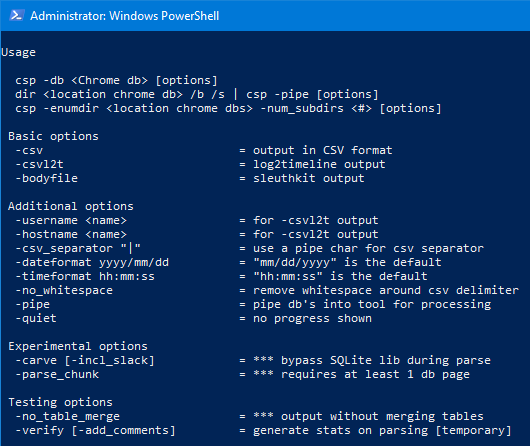
Below is an example of running the tool in its simplest form. Without explicitly setting any options, the tool will use will default to the SQL Select-type parser. The parsed output will dump to the screen, unless one redirects the output to a file.
c:\> csp -db c:\dump\History -csv > out.csv
To process multiple databases one would use the -pipe option while enumerating a folder and subfolder of databases, like so:
c:\> dir c:\dump\chrome_dbs /b /s /a | csp -pipe -carve -csvl2t > out.csv
Integrated Parsing Algorithms
The csp tool offers three possible parsing algorithms to choose from. They are as follows:
- 1. Default option. This option uses the internal SQLite library that is statically linked into the tool to perform a SQL-Select statement on the database under analysis. It is sensitive to corrupt databases and will not parse out records from unused or slack space.
- 2. Carve option. (-carve). This uses a TZWorks based set of algorithms to traverse the SQLite data structures to parse the records in the database. It relies on the database's schema and internal tree-based structures in the database to find the data. This option appears to work fine even if the database cannot be opened via the standard SQLite library. When corruption is present, this option will skip bad records and attempts to go to the next one. This option also looks at unused space for any records that may be present using the -incl_slack option.
- 3. Signature-base option. (-parse_chunk). This option does not make use of the SQLite schema or tree-based structures to locate records. Instead, it looks for certain signatures to locate records and parse them. Empirical testing has shown this approach works from either a good database, corrupted database or a partial blob of a database. While this option can pull valid records, it truncates the data when a record spans multiple SQLite-pages. For any records that are truncated, the output will be annotated with a flag identifying it as such.
For more information
The user's guide can be viewed here
If you would like more information about csp, contact us via email.
Downloads
| Intel 32-bit Version | Intel 64-bit Version | ARM 64-bit Version | ||||
| Windows: | csp32.v.0.27.win.zip | csp64.v.0.27.win.zip | csp64a.v.0.27.win.zip | md5/sha1 | ||
| Linux: | csp32.v.0.27.lin.tar.gz | csp64.v.0.27.lin.tar.gz | csp64a.v.0.27.lin.tar.gz | md5/sha1 | ||
| Mac OS X: | Not Available | csp.v.0.27.dmg | csp.v.0.27.dmg | md5/sha1 | ||
| *32bit apps can run in a 64bit linux distribution if "ia32-libs" (and dependencies) are present. | ||||||