Event Log MessageTables Offline (elmo)
Introduction
elmo is a prototype command line utility to assist the analyst in pulling message table data from providers with the objective of integrating these messages to events that are logged in the Windows event log.
The Windows event log conserves space using a number of mechanisms. One way is to reference the provider for each event along with unique event information in the log and store the more common information in a resource binary. The term provider, as used here, is the source of the event that was generated and is recorded in the event log. This can be one of the running services, drivers, or applications. Reconstruction of the complete message for an event that is logged therefore requires one to pull the common information from the resource that houses the provider's infomation. elmo is a utility to help the analyst do this.
When architecting elmo, our objective was to have a self-contained way to pull all the appropriate message tables from a target box and archive this data into a database that allows for easy retrieval. SQLite was chosen as the database engine, since it is lightweight, portable and ubiquitous across various operating systems.
elmo fills a need in the Windows event log parsing and reconstruction of logged events. At this point in time, however, since it is still new, it should be considered prototype in nature.
How to Use elmo
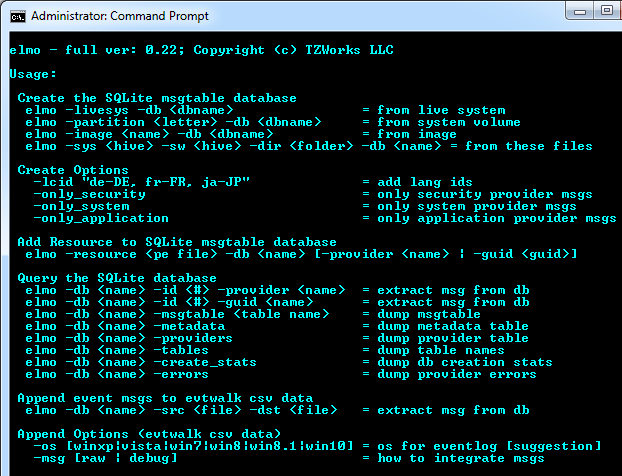
The screen shot below shows all the options available. The options are grouped into categories that equate to three basic functions:
-
- Create a SQLite database of Provider message tables
- Query the database to find specific data within the database
- Analyze the CSV data produced by the TZWorks tool evtwalk and annotate the CSV data with message data
Database Creation
To make elmo handle a number of different use-cases, we designed the tool to pull data from:
-
- a live box
- 'dd' image of a system volume
- a mounted system volume image that was extracted from another box
- discrete files pulled from a target box
For some of the database creation use-cases, elmo needs to run at administrative privileges. Once the database is created, elmo can be used for event log message re-creation and can be run at the typical user privileges.
The simplest way to create an elmo database, is to just run elmo on the target box and select the -livesys option, as shown below:
elmo64 -livesys -db test.db
From the above command, elmo will scan all the providers identified by the System hive (and depending on OS version, the Software hive as well) of the Windows registry. From each provider found, it will then parse each of the PE resources that were identified and extract the message table data. The provider, PE resource stats, and message table data is then archived into the database.
Database Query
One can use SQLite tools to query the database, or one can use the built-in elmo commands to enumerate any of the tables, their contents, or to search for matching messages given an event ID and its associated provider. Depending on the mixture of PE resources used during the elmo database creation phase, multiple candidate messages could be displayed for a given Event ID and Provider.
Below is an example where we created a single database from both Win7 and WinXP images and queried an event identifier 615 from the Security provider. The PE resource file used by the Security Provider for both Win7 and WinXP is msaudite.dll. While most PE resources spanning multiple operating systems have similar ID messages, some do not, like that in the example below:
elmo64 -db test.db -id 615 -provider security
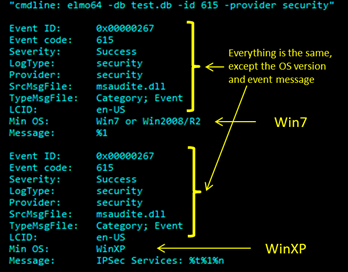
In this case, the first message is just the string "%1" and the second is the message "IPSec Services: %t%1%n". The "%1" is the way Microsoft defines a placeholder for a string argument. The data for the string argument is taken from the parsed event log and substituted into the message. The other variables, %t and %n are for a tab character and line feed character, respectively. So, while this example has a very short message, it was shown to enlighten the user that the combination of Provider and Event ID do not necessarily yield unique messages. As operating systems are enhanced, the names of many of the system PE resources stay the same, but their respective message tables may or may not change.
Using elmo to Analyze evtwalk Parsed Event Data
evtwalk is a TZWorks command line tool for parsing Windows event logs and outputting the results in a CSV fashion. While evtwalk pulls all the data available from an event log, it doesn't try to locate and extract the message table from the PE resource. To fill that need, we therefore added the functionality into elmo. So, if one has the updated version of evtwalk (v0.30 or later), one can take the CSV output from evtwalk and pass it into elmo. elmo in turn will analyze the CSV data and extract certain fields (like the provider and event ID for each record) and look up an associated message table. After this, elmo will perform argument substitution by taking the parameter data from the CSV file and generate a message which then gets appended to the CSV data. To ensure there is no corruption with the original CSV data, a new CSV file is created, which is identical to the original evtwalk CSV file inputted, but adds a couple of extra fields to each record. These fields include: (a) message translation and (b) task category translation.
This option should be considered experimental, since a number of conditions need to be satisfied for the above process to work. First, it assumes that resulting CSV file produced by evtwalk has all the fields needed by elmo populated. Basically this means that if you run evtwalk in a mode that does not filter any fields, then it should work. If filtering is used and the required fields needed by elmo are filtered out, then the results will be unknown. Second, the CSV file needs to have the required field header names and argument syntax for elmo to extract the proper field during its analysis. If one is using the latest version of evtwalk, then this latter requirement is satisfied
As an example, below is Event ID 7036 rendered from evtwalk. Highlighted with numbers are the locations of data used by elmo to perform automatic lookup and message translation.
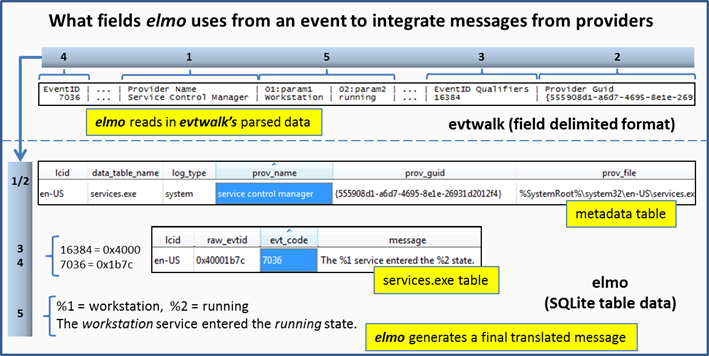
The key fields are: (a) Provider name and GUID (shown as 1 and 2 above), (b) Event ID and Qualifier (shown as 3 and 4 above), and (c) any string arguments (shown as 5). The first thing elmo looks at is the Provider name and/or GUID and looks up the Provider details in the metadata table. If a record is found, elmo then finds which PE resource message table was referenced by the Provider. With the PE resource message table, elmo then looks for a record with the target event ID and qualifier. If this is located, then the message is extracted. If there are any string arguments that need to be populated with event data, those fields are searched in the event data, and if found, extracted and substituted into the string arguments to make a completed message for that event.
For more information
The user's guide can be viewed here
If you have any questions about elmo, contact us via email.
Downloads
| Intel 32-bit Version | Intel 64-bit Version | ARM 64-bit Version | ||||
| Windows: | elmo32.v.0.46.win.zip | elmo64.v.0.46.win.zip | elmo64a.v.0.46.win.zip | md5/sha1 | ||
| Linux: | elmo32.v.0.46.lin.tar.gz | elmo64.v.0.46.lin.tar.gz | elmo64a.v.0.46.lin.tar.gz | md5/sha1 | ||
| Mac OS X: | Not Available | elmo.v.0.46.dmg | elmo.v.0.46.dmg | md5/sha1 | ||
| *32bit apps can run in a 64bit linux distribution if "ia32-libs" (and dependencies) are present. | ||||||